HTTPS has been on an ever-increasing popularity rise since Google announced on August 6th, 2014 that HTTPS will become a ranking signal. Google’s goal behind this HTTPS website ranking boost is to create a safer web surfing experience for online users. Google enticed webmasters worldwide to create a safer web experience for users by offering a ranking boost in return for HTTPS website implementation.
Google’s strategy has worked, as the graph below presents, “% of HTTPS pages loaded in Chrome” over time.
Note: I added Google’s HTTPS ranking signal announcement for clarity.

What is HTTPS, and how does it work?
HTTPS stands for Hyper Text Transport Protocol Secure, which is the secure connection protocol for HTTP, which is used to navigate between websites via your browser.
Difference between HTTP and HTTPS:
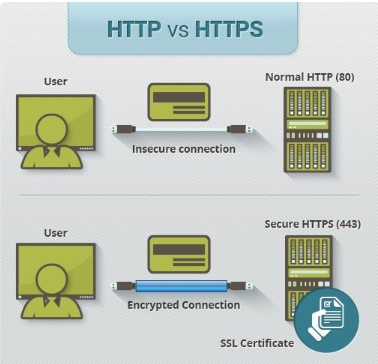
SSL certificates and HTTPS
Before I explain how HTTPS or certificate?
- An SSL (Security Socket Layer) certificate can be purchased by a third party or hosting provider. The certificate is set up and registered to www.example.com.au. The registration will certify the website's identity and assign an authentication ID number. This authentication number will be used to create an encrypted connection.
- Once the SSL certificate is registered, it enables the following:
- The possibility of “www.example.com.au” to have a HTTPS version.
- A green secure padlock feature or green bar is present in the URL when it loads in the browser.

- The certificate creates a uniquely encrypted data connection or SSL connection that is only operational with the HTTPS version of the website.
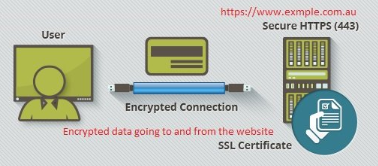
- Once the site is operating on HTTPS, it only encrypts data going to and from the website.
How does HTTPS work?
- A user wants to access https://www.example.com.au from their browser.
- The user’s browser is making a connection with the website.
- As the browser is making the connection, the SSL certificate verifies that https://www.example.com.au matches the registered identity and provides a secure connection with the browser.
- Once the connection is set up between the user’s browser and website – this is called a “handshake”.
- The “handshake” determines which type of encryption is used between the browser and the website. The type of encryption will be based on the type and level of encryption provided by the SSL certificate registered for the website.
- Now, data going to and from the website is securely encrypted. This data includes names, phone numbers, addresses, emails or even credit card information. When the data reaches its destination, the data becomes decrypted.
Common HTTPS myths
Now, it’s important to note before I go on any further I am not against having HTTPS security. I believe that with the large amount of demand generated for HTTPS from Google, web developers, SEO’ers and SSL providers, there is a lot of misinformation or assumptions about HTTPS.
It has come to a point where certain people think it’s a magic bullet to protect their website from hackers or malicious actions. To clear things up, I have listed the largest myths that I have come across about HTTPS as well as their underlying truths:
Myth: SSL encrypts data everywhere.
Truth: SSL only encrypts data in motion going to and from a website, NOT at rest points. Companies should always secure their data to a disk or offsite / offline, regardless of how long it will be stored.
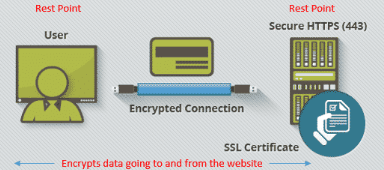
In other words, the vulnerability occurs when the data is decrypted at the user or server rest point. That is where a hacker can strike and collect decrypted information. Users should be using firewalls and anti-virus software for precautions. Websites need to look at storing information in secure servers, offline or in remote access cloud solutions.
Myth: My website is secure because it is HTTPS, data encrypted and has a green lock appearing on my URL in browsers.
Truth: Browsers have no solid method to understand how secure your website is from a broader sense apart from the SSL certificate on your website.
The green icon lock that browsers use to denote a secure connection is too easily misconstrued as a signal that the site is “secure”. Just because a site uses HTTPS doesn’t mean it’s not storing sensitive information, such as passwords or credit card information, in a non-secure manner somewhere else.
Myth: Having your data encrypted means it cannot be stolen.
Truth: Unfortunately, there is no 100% fail-safe method to protect encrypted data from being stolen. However, the benefit is if your data were to be stolen, it would be difficult for anyone to decrypt the information since encrypted data cannot be decrypted without a decryption key.
Myth: HTTPS slows down websites.
Truth: HTTPS on its own has no real noticeable effects on website speed.
Myth: SSL certificates are only for banks or e-commerce stores.
Truth: If you’ve got data about customers, products, employees, or the market that you believe is sensitive, then you should always encrypt it.
Overall, HTTPS is a great first step for increased online security, but more steps must be taken beyond HTTPS for greater online security. As highlighted in this article, HTTPS has its own vulnerabilities and isn’t a magic bullet for online security. Additional steps must be taken, such as firewalls, anti-virus software and server encryption, to improve online defences against data breaches and hackers.
Written by
Roy Zhai